In 2026, digital marketing has become a battle of algorithms. On one side, you have businesses trying to reach customers; on the other, you have Meta’s AI-driven security systems designed to crush spam.
For marketers and IT managers, the dreaded "Account Banned" notification is often a mystery. You didn't send offensive content. You didn't scam anyone. So, why were you blocked?
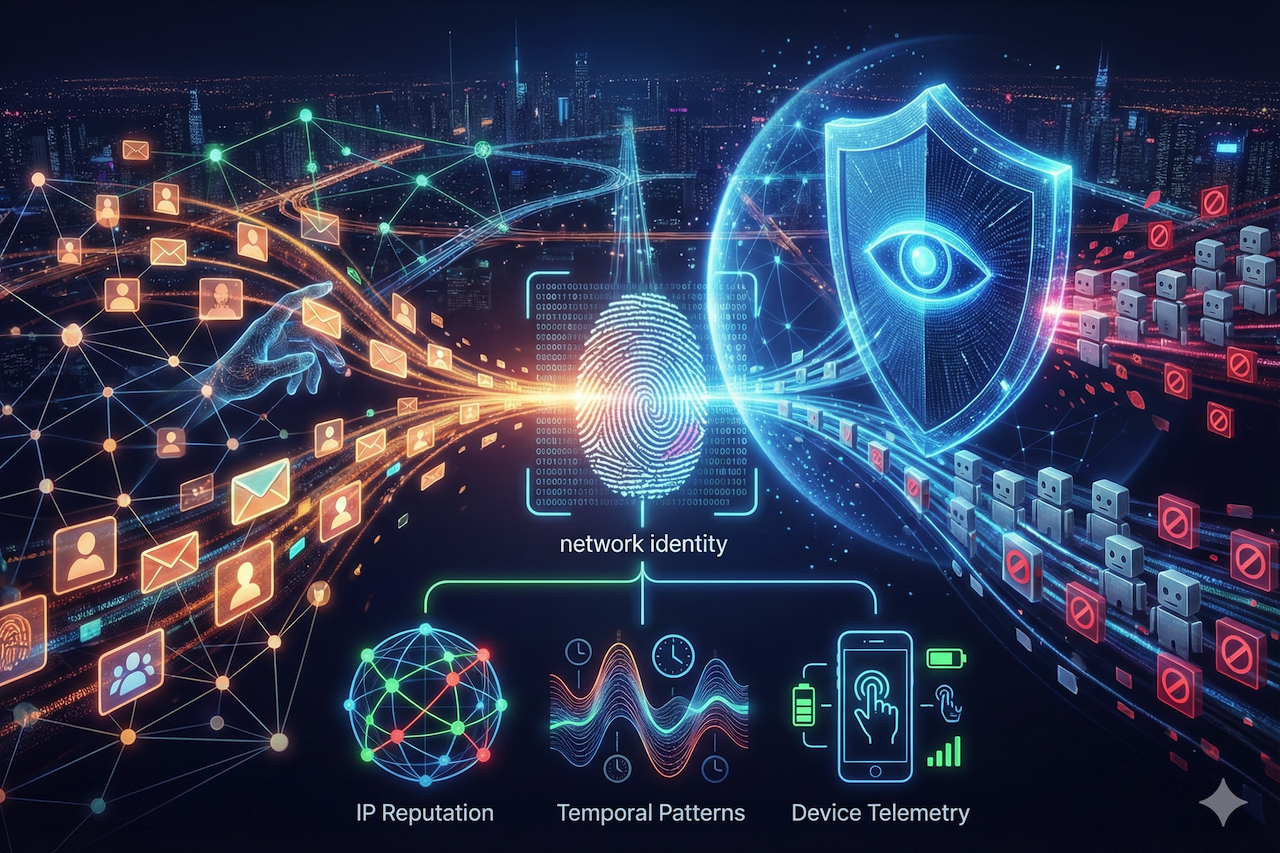
The answer usually lies in the network layer. WhatsApp’s anti-abuse systems no longer just read what you send; they analyze how you send it and where it comes from. If you are checking your IP on iplocation.net, you already understand the importance of network identity. Here is a technical breakdown of how to align your network hygiene with WhatsApp’s 2026 compliance standards.
The "Fingerprint" Analysis: It’s Not Just About the IP
When a message leaves your device, it carries metadata that forms a "digital fingerprint." Security algorithms analyze three core metrics to decide if you are a human or a bot:
- IP Reputation and ASN Trust: Not all IP addresses are equal. If you are routing traffic through a cheap data center proxy (often used by scrapers), your IP has a low "Trust Score." WhatsApp flags traffic coming from these ASNs (Autonomous System Numbers) as high-risk. In contrast, residential IPs, the kind assigned by ISPs like Verizon or Vodafone, carry high trust.
The Risk: Using a shared VPN often puts you on a "dirty" subnet. If a single user on that subnet spams, the entire range is blocked. - Temporal Patterns (The Robot Rhythm): Humans are inconsistent. We type, pause to drink coffee, and make typos. Bots are perfect. If your current tool sends messages at exact 5-second intervals (e.g., 0, 5, 10), you are broadcasting a "bot signal." In 2026, heuristic detection engines spot this mathematical perfection instantly.
- Device Telemetry: Real mobile devices send signals about battery level, screen interaction, and network latency (jitter). Web-based scripts often lack this telemetry, making them easy targets for automated bans.
Engineering a "Human-Like" Workflow
To operate safely, you don't need to hide; you need to blend in. You must engineer your traffic to look indistinguishable from organic user behavior.
This requires moving away from basic scripts to intelligent automation platforms, such as WhatsApp CRM solutions, which are built on a compliance-first architecture.
1. Implementing Randomized Jitter
A safe automation tool never uses fixed intervals. Instead, it applies randomized delays.
- Bad Workflow: Send every 10 seconds.
- Safe Workflow: Send message A, wait 12 seconds. Send message B, wait 45 seconds. Send message C, wait 8 seconds. This “jitter” mimics the natural pauses of a human thumb typing on a screen.
2. The “Warm-Up” Protocol
New accounts operate in a temporary “sandbox” period. If you register a number today and send 500 messages tomorrow, the account will likely be banned by noon. Professional software automates the warm-up phase to reduce this risk.
- Day 1–3: Engage in two-way conversations with known contacts to establish a high response rate.
- Day 4–7: Send 20–50 outbound messages.
- Day 8+: Gradually scale message volume based on account health.
The Role of Built-in Security Protocols
Finally, security isn't just about network tools; it requires an intelligent execution layer.
This is why successful teams use a dedicated WhatsApp CRM. It does more than store chats; it acts as an active security shield with built-in anti-ban protocols.
Modern platforms, such as WADesk, come equipped with native protection features designed to keep your IP reputation clean:
- Number Validation: Sending messages to non-existent or inactive numbers is a common signal associated with abusive messaging patterns. Validating numbers before sending helps reduce delivery failures and minimizes the risk of reputation damage caused by repeated hard bounces.
- Smart Throttling: Sending volume should be monitored to stay within platform tolerance levels. Automated throttling mechanisms can pause or slow message delivery when activity approaches predefined thresholds, helping to avoid sudden spikes that may trigger enforcement actions.
Conclusion: Compliance is Your Best Defense
In 2026, trying to outsmart the algorithm with "IP masking" or "anti-detect browsers" is a losing game. The AI is too fast.
The only sustainable strategy is emulation and compliance. By using high-quality network connections, simulating human latency, and respecting user opt-outs, you can build a high-performing, secure marketing channel.
Don't let a bad network configuration destroy your business assets. Check your IP, clean your list, and automate responsibly.
Featured Image generated by Google Gemini.
Share this post
Leave a comment
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.


Comments (0)
No comment